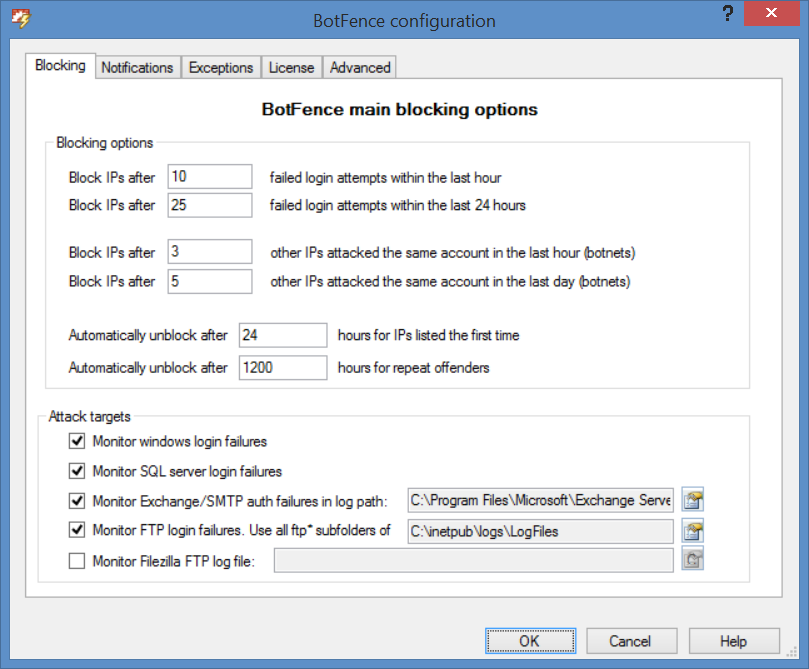
BotFence Configuration: Main blocking options
These are the main blocking options in the BotFenceAdmin configuration. You can configure which event sources BotFence will monitor and after how many failed logins it will block the attacking IP address in the firewall.
Parameters on this page:
- Blocking options: Define after how many failed login attempts any attacking IP will be blocked ans when it will be unblocked again. The first two values are the number of attacks (inside 1 hour and 24 hours) from the same IP that will cause the IP to be banned. The second pair of values configure the number of other IP's that failed to log into the same account inside the same 1 hour / 24 hours period. These are so-called botnets, whole networks of computers that have been hijacked to hack your system.
- Attack targets: Configure which event sources will be monitored for failed logins.
- Windows login: remote desktop login failures
- SQL Server: SQL server is one of the main targets of hackers - they always go for the superuser account "sa".
- Exchange/SMTP: Hackers also try to find login via SMTP AUTH - both to use your server as a relay and to later try the same passwords via rdp. BotFence will try to read the path to the receive connector protocol log files via Exchange shell command but you can configure the correct path here as well.
- FTP: In our own case FTP was the #1 attack target. Hackers seem to have advanced automated tools that try vast password databases here. You also need to configure the folder where BotFence will find the FTP subfolders with the FTP log files since this feature is based on realtime log file analysis.
- Filezilla FTP: Filezilla is an alternative FTP server that is often used and we personally could never get the auto-block option in that software to work. But of course BotFence takes care of that.
- Missing something?: Please let us know if you have other sources of attack information in your system. We are happy to include them in the next version of BotFence. Email our support!